I use the Fidelity app to manage a lump of rainy-day, retirement money. One of the features I love about the app is the home screen, where it summarizes today’s “movers” (best and worst performing) among the stocks and funds I’ve invested in. Now, this home screen doesn’t need to tell me how many shares of each I own or how much money I’ve made or lost, but it quickly tells me if I need to be paying attention. It gives me personalized, public information.
—or at least it would, if it didn’t require me to log in to see it.
Requiring a user to authenticate to view non-sensitive content lowers user engagement by introducing an annoying UX hurdle and adding security risk.
Bricking the UX
We all know logging in is a pain in the butt. We have too many accounts and too many passwords across too many devices. Identifying yourself hasn’t yet hit its own Golden Age. We’ve not yet figured out how to be most effective/secure without being a nuisance. Passwords are no good at saying who you are, password managers simply shift risk into a dense pocket, two-factor is sometimes better but can also be a big headache.
Unfortunately, we treat logging in as a binary permission. You are logged in, or you aren’t. All “you” information, regardless of sensitivity, is tied to your active session. In the case of the Fidelity app, that means a lost opportunity to regularly view one-click information—because my login session expires every few minutes.
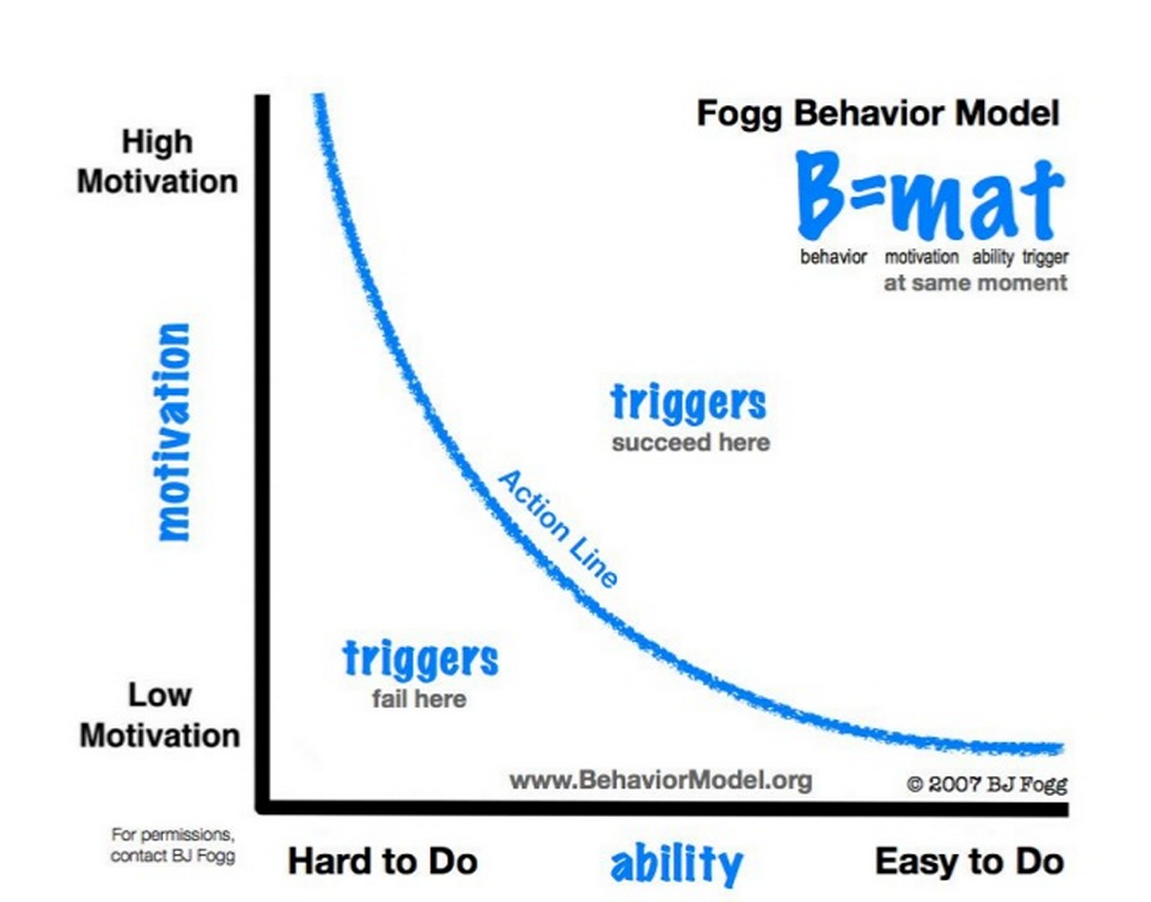
More annoying means less engaged and fewer visits. As a user, every time I launch any app on my phone, or browse to any website on my computer, I’m taking a snap litmus of effort versus motivation. This is best illustrated by the Fogg Behavior Model, where a successful action only exists when motivation (positive or negative) exceeds the user’s ability and convenience in performing a task.
If my app cached a list of my portfolio tickers (without the number of shares, etc.) I’d have at-a-glance access at any time of day, without needing to re-authenticate for each peek.
Security Risk
Aside from being annoying, this guise of security actually means my application or website is less secure. This week, I was at a hotel with *gasp* an open wifi network. I opted to not check any of my sensitive accounts.
Increasing the frequency of login also increases:
- Prying Eyes
The number of times someone might see you logging in—i.e., fat-fingering on the subway. - Shared Network Risk
The number of times you log in within unsafe networks, like the hotel example, or coffee-shop hotspots. - User Error
The number of times you might lock yourself out of an account for mis-typing on the go.
Reserving authentication for security-relevant content and tasks, increases the operational security of your product.
Progressive Authentication
The best work I’ve seen lately, is invisible. Microsoft calls it progressive authentication. Related to the progressive disclosure technique we use in the information architecture world, progressive authentication determines the amount of security necessary for any specific piece of content or function, and adds onion-peel layers of security.
Examples you’ve likely seen in the wild:
- Change my password
After logging in, needing to enter your password again. - Making a purchase (Amazon, e.g.)
After logging in, needing to enter your password again.
Those above examples are the most prevalent, but I’ve even seen some context-based examples:
- Unrecognized device or network
Needing to login again to connect. - Restarting your device
Needing to use 2-factor authentication—i.e., the iPhone requiring your pin even if you usually use your fingerprint.
Final Thoughts
In the case of the Fidelity app, I get why saved sessions aren’t a thing. (Though I’m not quite sure why a “remember me” checkbox exists.) However, I could immediately see three levels of progressive authentication:
- Level 1, My Market
No login required, with data refreshed every time I do log in. Show me non-sensitive information on launch, when I log in from recognized devices. Allow me to opt in/out. - Level 2, Portfolio Details
Require easy authentication to view account balances and other sensitive information, but without the ability to make changes. (For example, a pin usable on trusted devices only.) - Level 3, Transactions and Changes
Require two-factor authentication and/or enforce operational security when viewing extra-sensitive information, making transactions, or changing security settings.
Improving access to frequently needed low-sensitivity content encourages me to use your product more frequently, in a convenient and safe manner. In the end, it not only promotes engagement, but instills brand loyalty.